Active Directory Users and Computers: User Account information for the GFI EndPointSecurity Logger Service must also be provided - this must be a domain administrator - or the local system account can be used, see Figure 1. By default, reports that show things like device usage summary, trends and statistics, most active machines and users, technical reports, etc. This wizard takes us through the most important steps in configuring the product. Much of this can be controlled with permission settings on files, folders, database tables, websites etc. 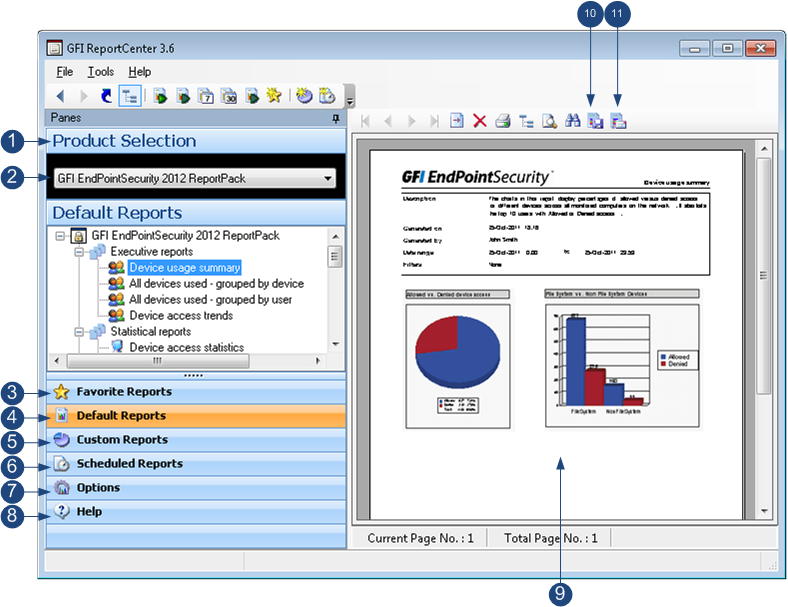
| Uploader: | Mosida |
| Date Added: | 21 November 2010 |
| File Size: | 39.63 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 8662 |
| Price: | Free* [*Free Regsitration Required] |
Free Active Directory Auditing with Netwrix. Heidelberg Posted On March 8, So, what can we do about this? In Microsoft Windows Vista, administrators can configure which users are allowed or denied access to different portable storage devices - this level of granular control however, cannot be extended to devices without a file system. Technological breakthroughs have made available devices that boast:.
If the remote computer is not online we get an error message like the one in Figure 7. Many lines endpointsecurihy business face increased requirements which demand more protection and tighter control over client records and confidential information. General gives access to licensing information and support information, etc.
Device usage reporting | GFI EndPointSecurity
Figure 10 shows how Active Directory security groups are connected to access permissions for Storage Devices. On the server-side, policies are configured and settings are pushed to the clients.

This wizard takes us through rsportpack most important steps in configuring the product. The right information in the right place just changes your life. I recommend you to go and download the trial and test this powerful piece of software.
Where can I download the GFI EndPointSecurity ReportPack and or the GFI ReportCenter?
Development of support for bit Windows operating systems is currently underway and will be available in a future release. After installing GFI EndPointSecurity and deploying the agent to the server we can see 3 new services 2 for the server and 1 for the optional local agent:.
Steward Brand joined the first Hacker Conference in and stated the following: Both default and customized reports can be scheduled to run in a given interval for 'today', 'yesterday', 'last 7 days', 'last 30 days' or a custom date range Figure repprtpack A data thief can get away with more precious data in his pockets, a negligent employee can dump more malware to the corporate computers and a malicious user can upload more illegal content to the corporate web servers than ever before - and in less time.
After setting up the different protection polices, computer accounts are endpointsecurlty added to these policies. We need to worry about: Join Our Newsletter Learn about the latest security threats, system optimization tricks, and the hottest new technologies in the industry.
Over 1, fellow IT Pros are already on-board, don't be left out! Much of this can be controlled with permission settings on files, folders, database tables, websites etc. Active Directory Users and Computers: So, what devices are we talking about?
If some user needs to be able to read a specific file, or a table in a database, that information can also be copied to another "uncontrolled" destination or device by the same user, which might not be in the interest of the company. The point is that internal users may deliberately or accidentally copy confidential information to these devices, introduce malicious code malware of any kind or transfer other unwanted data to the corporate network.
GFI EndPointSecurity ReportPack Is Now Available
GFI EndPointSecurity provides system administrators with the ability to exert almost the exact same level of granular control over all bit versions of WindowsXP, based computers and all devices without a file system. It's time to look at a product that can give us some countermeasures against these potential security threats.
First, we need a written corporate portable storage control policy as part of the company's IT security policy.
Another example is people leaving the company to work with a competitor, the dishonest ones may use the information acquired to gain an edge over their previous employer.
I understand that by submitting this form my personal information is subject to the TechGenix Privacy Policy.
GFI EndPointSecurity ReportPack Download
The deployment report shows us the status of the remote agent installation process, see Figure 6. An experienced user would be able to spot the service running in the background, but apart from this, all the users will see is Windows default block messages like "Access denied" when trying to do endpojntsecurity that is out of the users "scope".
To put it more precisely:

No comments:
Post a Comment